Contact Us
+91 820 810 7030
24 Aug 2024
Unveiling the Evolution: From DevOps to DevSecOps - Enhancing Security in Software Development

Introduction
Welcome to my take on the evolution of DevOps! Before diving into DevSecOps, the important thing for you, dear reader, is to get familiar with the Key Teams in the Software Development process, and what are the challenges we face before DevOps.
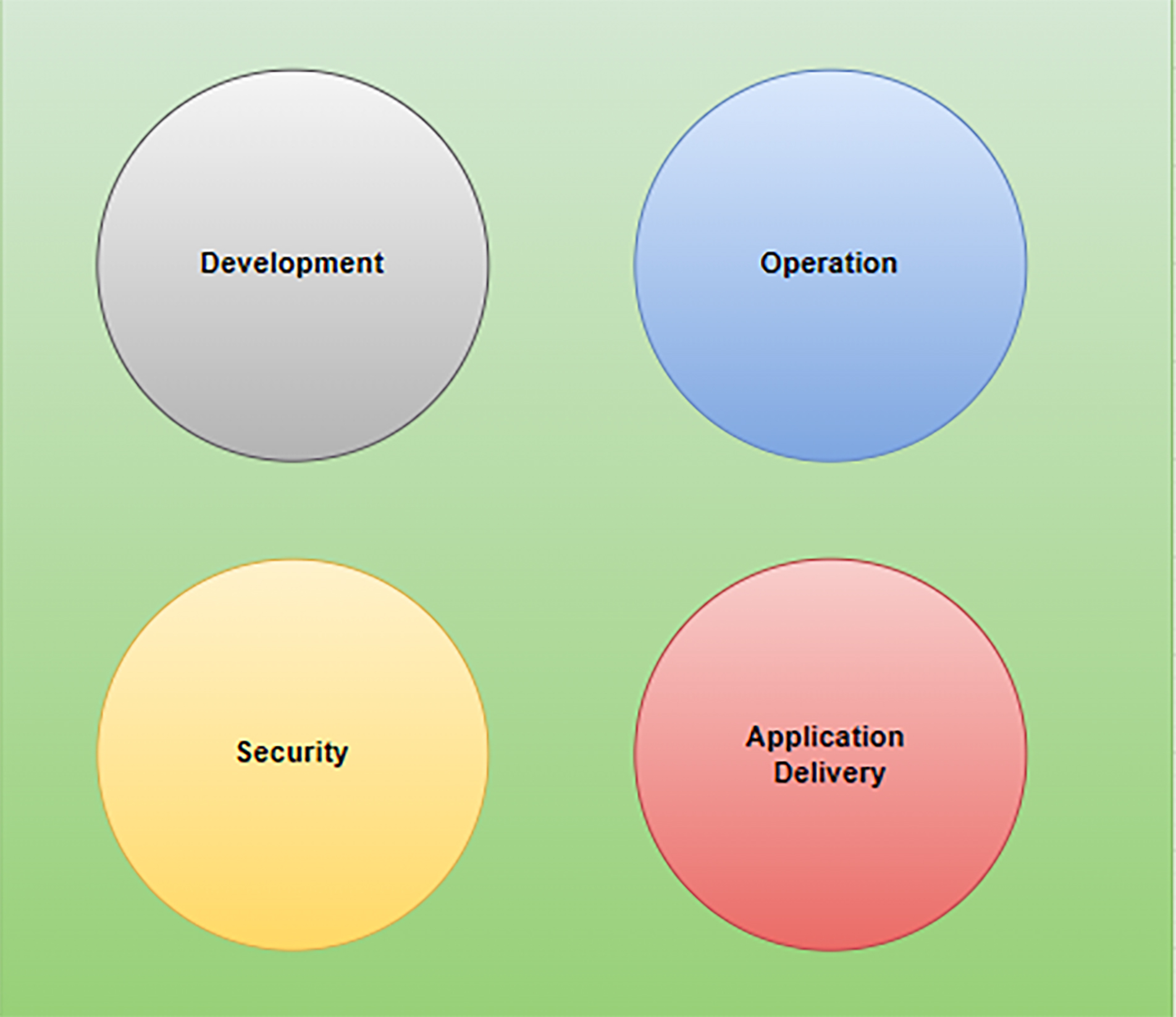
Key Teams in Software Development
- Development Team: Responsible for developing and testing applications.
- IT Operations: Prepares and manages the IT infrastructure for hosting applications.
- Application Delivery: Deploys the source code to the infrastructure managed by IT Operations.
- Security: Ensures the security of infrastructure, networking, and applications.
Pre-DevOps Era:
In the Pre-DevOps era, the software development process was often fragmented and siloed, leading to several inefficiencies and challenges:
- Development Team: Developers focused mainly on writing code and performing initial testing. They had little involvement in the deployment and operational aspects of the application, leading to potential issues when the code was handed off to other teams.
- IT Operations: The IT Operations team managed the infrastructure required to host the application. Minimal interaction with the development team resulted in misalignments and delays when the application was deployed, as infrastructure needs and limitations were not fully understood or addressed during development.
- Application Delivery: The process of deploying the application was manual and error prone, resulting in longer release cycles and slower delivery of new features and updates to users.
- Security: Security checks were typically performed late in the development cycle, usually just before deployment. This meant that vulnerabilities and security issues were often discovered at the last minute, requiring rushed fixes that could introduce further problems or delays.
Collaboration and Automation
Collaboration was limited, and automation was rare. Manual processes dominated, making it difficult to achieve reliable software delivery.
DevOps Era
The advent of the DevOps era focused on improving teamwork, automating tasks, and boosting communication between teams. This helps to break down barriers and make the software development process more efficient and streamlined.
- Development Team: Works closely with IT Operations to ensure that the code they write is both functional and deployable. This collaboration ensures that the development process considers operational requirements, reducing issues during deployment.
- IT Operations: Collaborates with developers to streamline the provisioning and management of infrastructure. This cooperation helps in creating an environment that supports efficient deployment and scalability, making sure that infrastructure needs are met in sync with development efforts.
- Application Delivery: Focuses on automating the deployment processes. Automation reduces manual errors and accelerates the release cycles, ensuring that updates and new features are delivered quickly and reliably.
- Security: Although not fully integrated into the early stages of development, security considerations begin to be addressed earlier in the process. This means that basic security measures and compliance checks are implemented during development, rather than as an afterthought, helping to identify and mitigate potential vulnerabilities sooner.
Collaboration and Automation
DevOps introduced continuous integration and continuous delivery (CI/CD) pipelines, enabling automated testing, deployment, and infrastructure provisioning. This era is characterized by:
- Increased Automation: Automated build, test, and deployment processes to ensure faster and more reliable releases.
- Shift-Left Approach:
Beginning to incorporate security and quality checks earlier in the development cycle.
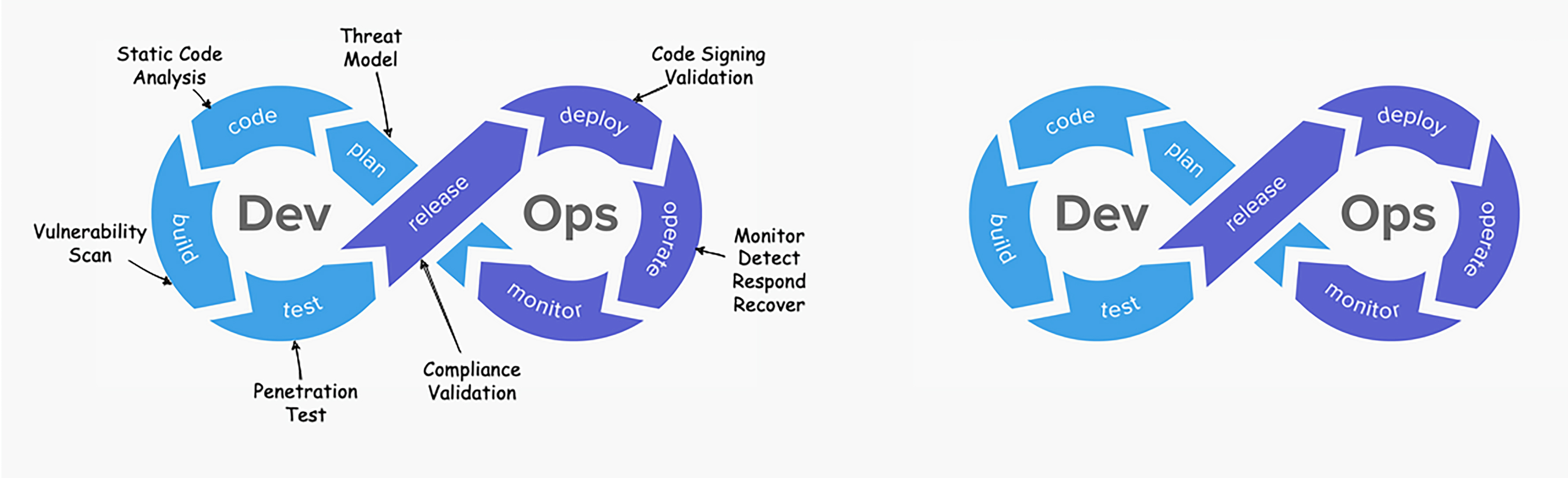
DevSecOps Era:
In the DevSecOps era, security is deeply integrated into every phase of the software development lifecycle (SDLC). This approach ensures that applications are secure from the ground up, through continuous collaboration and advanced automation. Here’s how it works:
- Integrated Security: Security practices are embedded throughout the SDLC. This means security considerations are part of every phase of development, from planning and coding to testing and deployment. This integration helps ensure that security is a primary focus and not an afterthought.
- Proactive Measures: The approach emphasizes early identification and remediation of vulnerabilities. By shifting security left, issues are detected and addressed much earlier in the development process, reducing the risk of critical vulnerabilities making it to production.
- Cross-Functional Collaboration: There is continuous collaboration among development, operations, and security teams. This collaboration breaks down traditional silos and promotes a shared responsibility for security, leading to more effective and cohesive security practices.
- Comprehensive Automation: Extensive use of automated tools for security testing and monitoring is a hallmark of the DevSecOps era. Automated tools like Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and continuous monitoring tools help in identifying and fixing security issues swiftly and efficiently, ensuring continuous protection throughout the development and deployment processes.
By embedding security into the entire lifecycle, adopting proactive measures, fostering collaboration, and leveraging automation, DevSecOps creates a robust framework for building secure and resilient applications
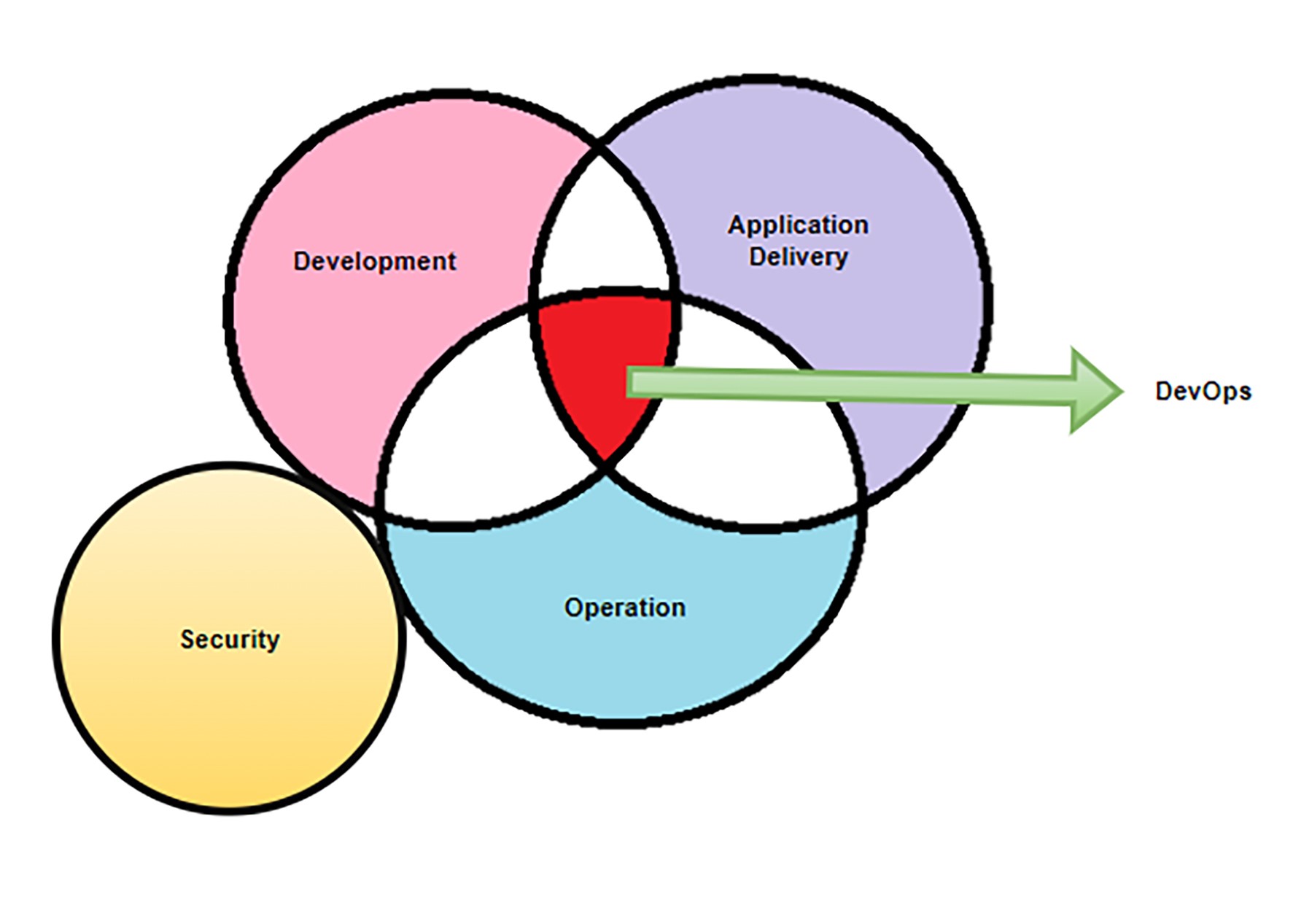
DevSecOps Era:
DevSecOps is a combination of Development, Security, and Operation. It is the practice of integrating security testing at every stage of the software. DevSecOps extends the principles of DevOps by fully integrating security into every stage of the software development lifecycle. This ensures that security is a shared responsibility among all teams.
- Development Team: Incorporates secure coding practices and works closely with security experts.
- IT Operations: Manages infrastructure with a focus on security and compliance.
- Application Delivery: Uses automated security testing tools as part of the CI/CD pipeline.
- Security: Engages from the start, embedding security practices and tools throughout the development and deployment processes.
The birth of DevSecOps:
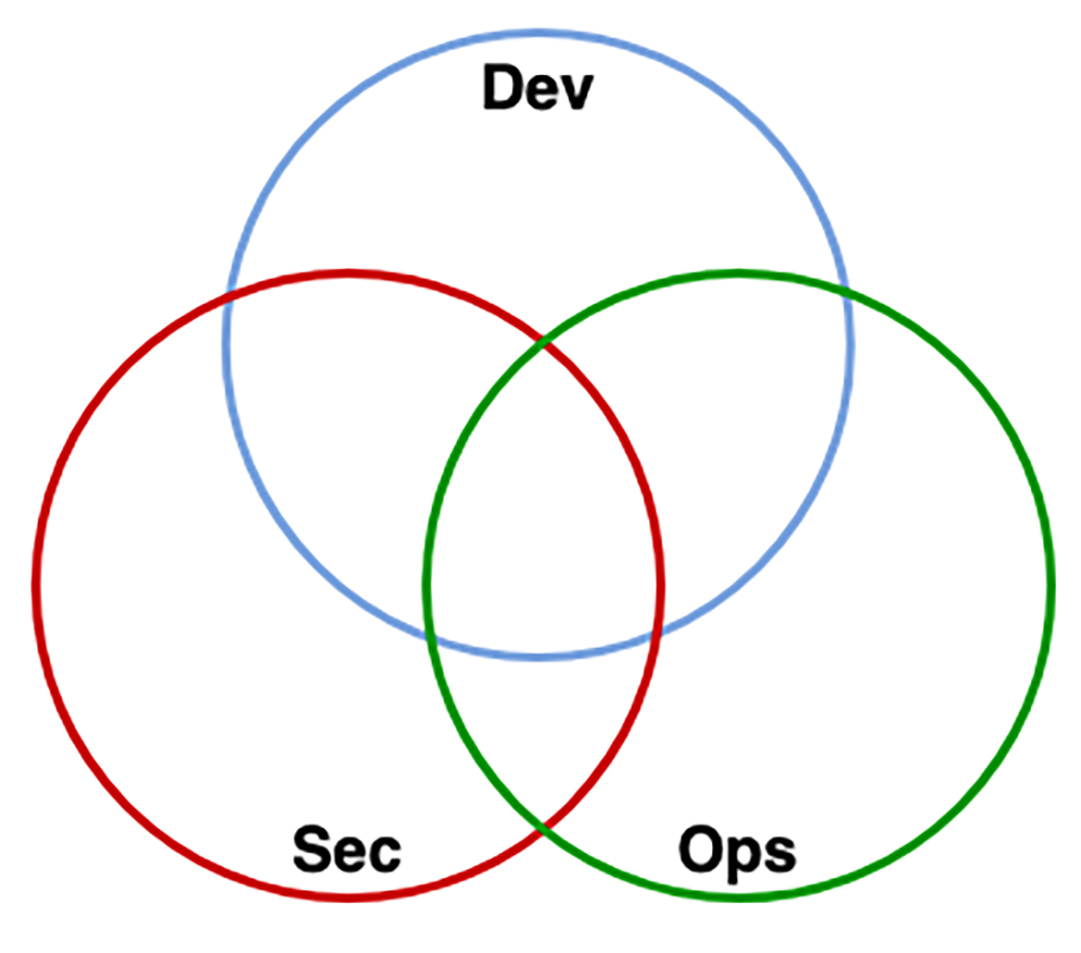
DevSecOps was introduced to address the evolving challenges and needs of modern software development. DevSecOps is a response to cyber threats and the need for security to be a fundamental part of software development. It collaboration, shared responsibility, and a shift-left philosophy among development, operations, and security teams.
Here are some key reasons why DevSecOps became a crucial addition to traditional DevOps practices:
- Cybersecurity Threats: Increasing frequency and sophistication of cyber threats necessitated a more proactive and integrated security approach.
- Shift-Left Philosophy: Embraced the "shift-left" approach, integrating security measures earlier in the development process to catch and address issues sooner.
- Shared Responsibility: Recognized security as a shared responsibility among development, operations, and security teams, fostering collaboration.
- Continuous Delivery Practices: Aligned with Agile and continuous delivery practices, ensuring security measures kept pace with the rapid deployment cycles.
- Automation Capabilities: Leveraged automation to efficiently identify, remediate, and prevent security vulnerabilities within the development pipeline.
- Regulatory Compliance: Addressed increasingly stringent regulatory requirements by integrating security practices in line with industry standards.
- Cost-Efficiency: Recognized that addressing security concerns early in the development process is more cost-effective than dealing with them later or after deployment.

Difference between DevOps and DevSecOps
| Sr. | Technical Aspect | DevOps | DevSecOps |
|---|---|---|---|
| 1 | Primary Focus | Continuous integration, delivery, and deployment. | Integration of security practices into the entire pipeline. |
| 2 | Security Integration | Security is addressed but often as a secondary concern. | Security is integrated at each phase, adopting a "shift-left" approach. |
| 3 | Security as Code | Limited emphasis on treating security as code. | Encourages treating security policies and controls as code, known as "Security as Code." |
| 4 | Automation for Security | Automation primarily focuses on build, test, and deployment processes. | Extensive use of automated security testing, code analysis, and vulnerability scanning. |
| 5 | Continuous Monitoring | Monitoring focuses on performance metrics and system health. | Extensive continuous monitoring for security threats, anomalies, and compliance adherence. |
| 6 | Toolchain | CI/CD tools are prominent, along with infrastructure provisioning tools. | Expands the toolchain to include security-specific tools like static/dynamic analysis, and penetration testing tools. |
| 7 | Collaboration Tools | Relies on collaboration tools for communication between Dev and Ops teams. | Extends collaboration tools to include security team participation, fostering cross-functional collaboration. |
| 8 | DevOps vs DevSecOps Roles | DevOps roles focus on development, operations, and automation. | DevSecOps roles include security engineers, penetration testers, and emphasize cross-functional security expertise. |
| 9 | Shift-Left Approach | The shift-left approach may not be fully realized in terms of security. | Embraces and fully implements a shift-left approach, emphasizing early integration of security practices. |
| 10 | Risk Management | Risk management is reactive, with focus on system performance. | Proactively manages security risks, identifying and addressing vulnerabilities before deployment. |
DevSecOps Tools that Use AI:
The integration of Artificial Intelligence (AI) into DevSecOps tools has revolutionized how security is managed in the development process. AI-driven tools enhance threat detection, automate security processes, and provide actionable insights. Some DevSecOps tools utilizing AI include:
- Snyk:
- AI Feature: Snyk uses AI for continuous monitoring and real-time vulnerability scanning of open-source dependencies.
- Purpose: It helps identify and remediate security vulnerabilities in third-party libraries and frameworks.
- Checkmarx:
- AI Feature: Checkmarx incorporates AI-driven static application security testing (SAST) for in-depth code analysis.
- Purpose: It identifies and mitigates security vulnerabilities in the source code during the development phase.
- Fortify:
- AI Feature: Fortify utilizes AI-powered security analysis to assess and manage application security risks.
- Purpose: It provides actionable insights for developers to address vulnerabilities and enhance overall security posture.
- WhiteSource(mend.io):
- AI Feature: WhiteSource uses AI algorithms for continuous open-source risk management and vulnerability detection.
- Purpose: It helps organizations manage and secure open-source components in their applications.
- SonarQube:
- AI Feature: SonarQube integrates AI-powered static code analysis for identifying security vulnerabilities and code quality issues.
- Purpose: It provides developers with feedback on potential security risks during the coding phase.
- NeuraLegion (Now part of Checkmarx):
- AI Feature: NeuraLegion leverages AI for dynamic application security testing (DAST) and automated penetration testing.
- Purpose: It helps identify and remediate security vulnerabilities in web applications.
| Technical Aspect | Snyk | Checkmarx | Fortify |
|---|---|---|---|
| Pros |
|
|
|
| Cons |
|
|
|
| Strengths |
|
|
|
Conclusion:
- DevSecOps integrates security into every stage of the SDLC
- Addresses challenges of traditional DevOps by incorporating security
- Utilizes AI-driven tools for proactive security management
- Emphasizes collaboration, automation, and continuous monitoring



